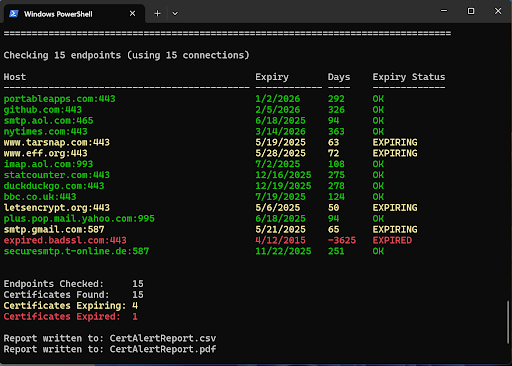
CertAlert FAQ
Commonly asked questions about our enterprise certificate monitoring and discovery tool
Frequently Asked Questions
- What Is CertAlert?
- System Requirements
- Certificate Expiry Monitoring
- Certificate Discovery
- Certificate Auditing
- Download & Run
- Feature Requests
- Scan Speed Configuration
- Multi-Platform Support
- Expiry Warning Period
- STARTTLS Support
- Alert Configuration
- Report Configuration
- IP Range Configuration
- Port Configuration
- SMTP Configuration
- Automation
- Including Certificates
- Report Fields
- SNI Support
- Config Editing
- CSV Viewers
What Is CertAlert?
CertAlert is our enterprise-grade certificate management solution that offers a comprehensive set of features, including:
- Network scanning to discover deployed SSL/TLS certificates
- Automated email alerts for certificates approaching expiration
- Advanced certificate analysis to identify security vulnerabilities
- Detailed reporting in both PDF and CSV formats
CertAlert System Requirements
CertAlert is compatible with all versions of Windows, starting from Windows 11 and Windows Server 2016 onwards. We are currently developing a Linux version of CertAlert. If you're interested in testing this version, please contact our team.
Is CertAlert A Certificate Expiry Monitor?
Yes, CertAlert is a comprehensive Certificate Expiry Monitor. It continuously tracks SSL certificates deployed across your networks and sends timely expiration notifications to designated recipients, ensuring certificates can be renewed before they impact your services.
Does CertAlert Discover Certificates?
Absolutely. CertAlert functions as a powerful Certificate Discovery Tool. It systematically scans your networks based on specified IP ranges (or a hosts file) and port ranges to locate deployed SSL certificates. The scan results are compiled into detailed reports that help identify potential issues such as weak algorithms, inadequate key lengths, or unknown certificate authorities.
Does CertAlert Audit Certificates?
Indeed, CertAlert serves as a comprehensive Certificate Audit Tool. It thoroughly scans your networks for SSL certificates and generates detailed reports that help identify potential compliance issues within your certificate inventory, ensuring your digital infrastructure meets security best practices and industry standards.
How Do I Download And Run CertAlert?
CertAlert is designed for easy deployment and use. Visit our Getting Started page for a step-by-step guide on downloading and running CertAlert for the first time.
Can I Request New Features?
Absolutely! We value customer input in our product development. If you have suggestions that would enhance CertAlert for your organization, please share them with us at [email protected].
Is The Scan Speed Configurable?
Yes, you can optimize scan performance by adjusting the number of concurrent outgoing connection attempts.
This is controlled by the Connections configuration value, which defaults to 256 as shown below:
<add key="Connections" value="256"/>
Does CertAlert Discover Certificates On Any Operating System?
Yes, CertAlert will attempt to connect to all endpoints you specify, regardless of the underlying platform. This includes Windows, macOS, Linux, Unix, and various network devices. CertAlert's platform-agnostic scanning ensures certificate discovery across heterogeneous enterprise environments.
Is The Certificate Expiry Warning Period Configurable?
Yes, you can customize the advance notification period for certificate expiration by setting the
WarningInterval configuration value. By default, it is set to 90 days as shown below:
<add key="WarningInterval" value="90" />
Can CertAlert Check For Certificates Used With STARTTLS?
Yes, CertAlert supports checking SSL certificates used with STARTTLS SMTP.
The default STARTTLS ports checked are 25 and 587. You can customize this via the SmtpStartTlsPorts configuration option:
<add key="SmtpStartTlsPorts" value="25,587"/>
How Do I Specify The Alerts I Receive?
CertAlert allows you to customize which events trigger alerts. The available options are:
- No Certificate Was Detected
- Certificate Is Expiring
- Certificate Has Expired
To specify which events should trigger alerts, adjust the EmailAlerts configuration setting:
<add key="EmailAlerts" value="EXPIRED,EXPIRING" />
How Do I Specify The Certificates Reported?
CertAlert lets you customize which certificate conditions appear in your reports:
- No Certificate Was Detected
- Certificate Is Expiring
- Certificate Has Expired
- Certificate Is OK (neither expired nor expiring)
Configure this by setting the ReportConditions value. The example below will only include
expiring and expired certificates in reports:
<add key="ReportConditions" value="EXPIRED,EXPIRING" />
How Do I Specify The IP Ranges I Want Scanned?
CertAlert supports both nmap-style (e.g., 178.125.139.1-162) and CIDR notation (e.g., 192.168.0.0/24) for IP ranges.
To use IP ranges, set UseIPRanges to true and specify the ranges with the IPRanges setting:
<add key="UseIPRanges" value="true" />
<add key="IPRanges" value="192.168.1.1-2,192.168.2.1-2,192.168.0.0/24" />
How Do I Specify The Ports I Want Checked?
CertAlert allows you to specify which TCP ports to check during scans. You can list individual ports and port ranges
using the Ports configuration setting. For reference on common SSL ports, see our
Common SSL ports article.
<add key="Ports" value="443,444,1-65,44000,45000-45500" />
Configuring Email (SMTP)
CertAlert can send email reports and alerts. To enable this
feature, you must configure your SMTP server settings within
the CertAlert.dll.config file.
Basic SMTP Setup
For most standard SMTP servers that do not require
authentication or a specific port, simply add the
SMTPServer key with your server address:
<add key="SMTPServer" value="smtp.mydomain.com" />
Advanced SMTP Setup (Authentication and Custom Ports)
If your SMTP server requires authentication (like a Gmail account) or runs on a port other than the default, you will need to provide more detailed configuration. The following example demonstrates a typical setup for Gmail:
<add key="SMTPServer" value="smtp.gmail.com" /> <add key="SMTPPort" value="587" /> <add key="SMTPRequiresAuthentication" value="true" /> <add key="SMTPUser" value="[email protected]" /> <add key="SMTPPassword" value="yourgmailpassword" /> <add key="SMTPUseSsl" value="true" />
Configuration Keys Explained
SMTPServer: The hostname or IP address of your SMTP server.SMTPPort: (Optional) The port number your SMTP server uses. Default is usually 25, but common alternatives include 587 (for TLS) or 465 (for SSL).SMTPRequiresAuthentication: Set to true if your server requires a username and password.SMTPUser: Your username or email address for SMTP authentication.SMTPPassword: Your password for SMTP authentication.SMTPUseSsl: Set to true to enable SSL/TLS encryption for the connection.
Note: Be sure to replace the placeholder values ([email protected], yourgmailpassword, and smtp.mydomain.com if using the basic example) with your actual SMTP server details and credentials.
How Do I Run CertAlert Automatically?
You can schedule CertAlert to run automatically on Windows using the Task Scheduler.
Important Considerations
- Set the "Start in" value in the Task's "Action" settings to the folder where CertAlert is located (e.g., C:\CertAlert). Although labelled optional in Task Scheduler, this step is required for CertAlert to find its configuration, licence, and log files correctly.
- Before scheduling, run CertAlert.exe once interactively from its final location (e.g. C:\CertAlert) using the same Windows user account that the scheduled task will run as. This ensures the EULA is accepted for that user in that location, preventing the automated task from getting stuck waiting for EULA input ('yes').
Steps for Windows Task Scheduler
- Unzip CertAlert to its final location, for example: C:\CertAlert
- Open Task Scheduler (Type "Task Scheduler" in the Windows Start menu).
- In the "Actions" pane (on the right), click "Create Task..." (Note: Do not use Create Basic Task).
- Configure the task using the tabs:
- Name: (On the General tab) Give it a descriptive name (e.g., "Daily CertAlert Scan").
- General tab:
- Select "Run whether user is logged on or not". (This often requires entering account credentials when saving the task). Run with the minimum privileges needed.
- Select "Hidden" (prevents console window popup).
- Triggers tab: Click 'New...' to define when it should run (e.g., Daily, specify time).
- Actions tab: Click 'New...'. Ensure Action is "Start a program".
- Program/script: C:\CertAlert\CertAlert.exe (Use the full path)
- Start in (optional): C:\CertAlert (Use the full path - REQUIRED)
- Conditions/Settings tabs: Review other options. Consider setting "Stop the task if it runs longer than:" (on the Settings tab) to a suitable duration (e.g., 4 hours).
- Click OK to save the task (entering credentials if prompted).
How Do I Include PEM Certificates In The Report?
To include PEM-formatted certificates in your reports, enable the PemCertCol setting in the configuration file:
<add key="PemCertCol" value="true"/>
How Do I Specify The Fields Reported?
CertAlert allows you to customize which fields appear in your CSV reports. Set any field to "true" to include it or "false" to exclude it. Here are the default settings:
<add key="HostCol" value="true"/>
<add key="IpAddressCol" value="true"/>
<add key="PortCol" value="true"/>
<add key="CommonNameCol" value="true"/>
<add key="IssuerOrgCol" value="true"/>
<add key="IssuerCol" value="false"/>
<add key="SubjectCol" value="false"/>
<add key="SigAlgCol" value="true"/>
<add key="KeySizeCol" value="true"/>
<add key="SerialNumberCol" value="true"/>
<add key="SelfSignedCol" value="true"/>
<add key="VerifiedCol" value="true"/>
<add key="SubAltNamesCol" value="true"/>
<add key="Sha1FingerprintCol" value="true"/>
<add key="NotBeforeCol" value="true"/>
<add key="NotAfterCol" value="true"/>
<add key="DaysTillExpiryCol" value="true"/>
<add key="ExpiryStatusCol" value="true"/>
<add key="PemCertCol" value="false"/>
<add key="ErrorInfoCol" value="true"/>
Does CertAlert Support Server Name Indication (SNI)?
Yes, CertAlert fully supports Server Name Indication (SNI), allowing it to correctly identify certificates on servers that host multiple websites with different SSL certificates. You can verify this by scanning an SNI-enabled site such as https://bob.sni.velox.ch.
When an SNI-supporting client connects to this site, it returns a certificate with the common name bob.sni.velox.ch. Clients without SNI support receive a certificate for alice.sni.velox.ch instead.
Which Editor Is Best for Editing CertAlert.dll.config?
We recommend NotePad++ for editing the CertAlert.dll.config file. It offers user-friendly interface and XML syntax highlighting. To enable syntax highlighting, select 'Language' from the menu and choose 'XML'.
What's A Good Lightweight CSV File Viewer?
Several options are available for viewing CertAlert's CSV reports:
- Microsoft Excel - Full-featured spreadsheet with advanced filtering
- CSVFileView (Free - NirSoft):
- Ron's Data Edit
Still have questions?
We're ready to help with any additional questions. Email us at [email protected]